
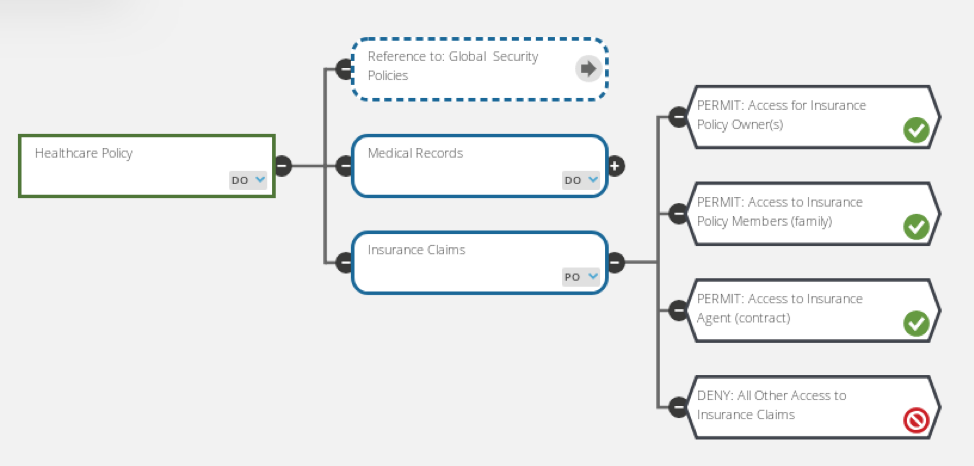
Figure 4 from Guide to Attribute Based Access Control (ABAC) Definition and Considerations | Semantic Scholar
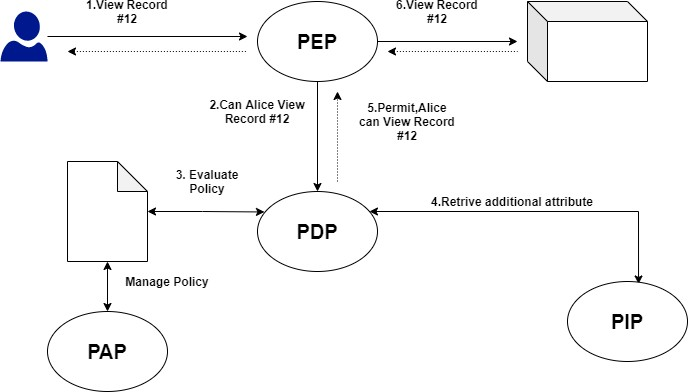
DZone: Why Attribute-Based Access Control - The Evolution from RBAC to ABAC in Data Access Control - Axiomatics

How to scale your authorization needs by using attribute-based access control with S3 | AWS Security Blog
Matthew Sanders and Chuan Yue Automated methods for generating least privilege access control policies. ACSAC '19

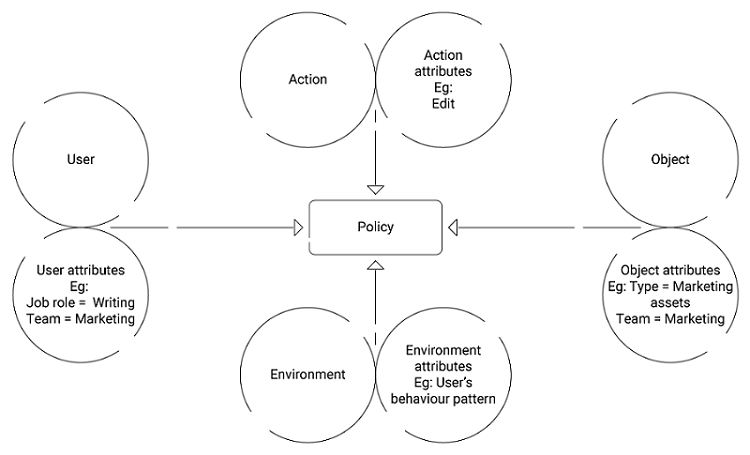
Five Cornerstones of ABAC: Policy, Subject, Object, Operation Type and... | Download Scientific Diagram



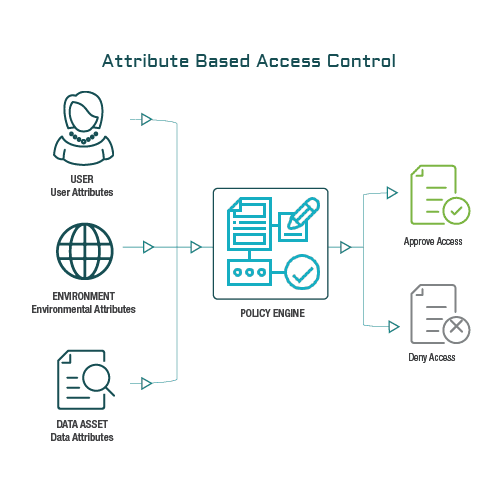

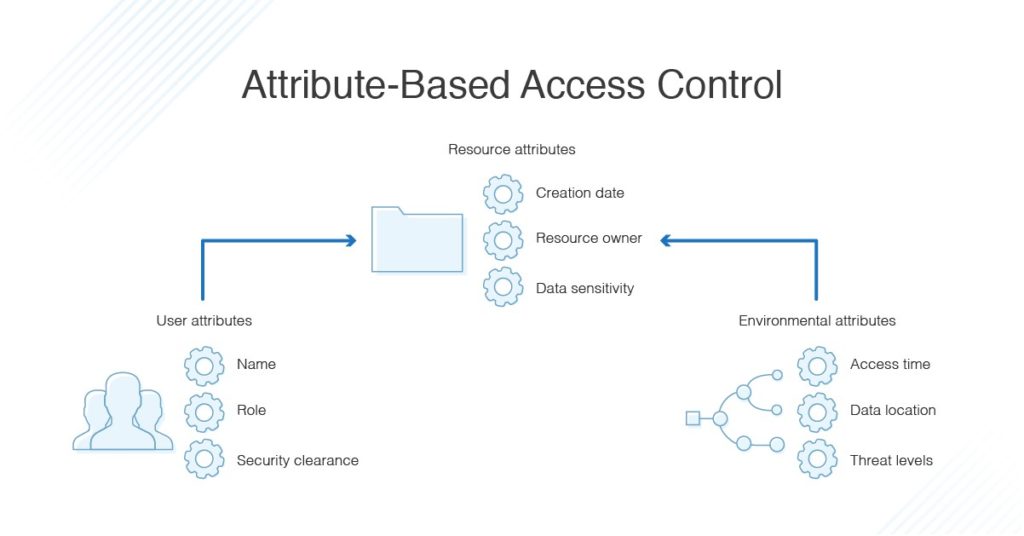

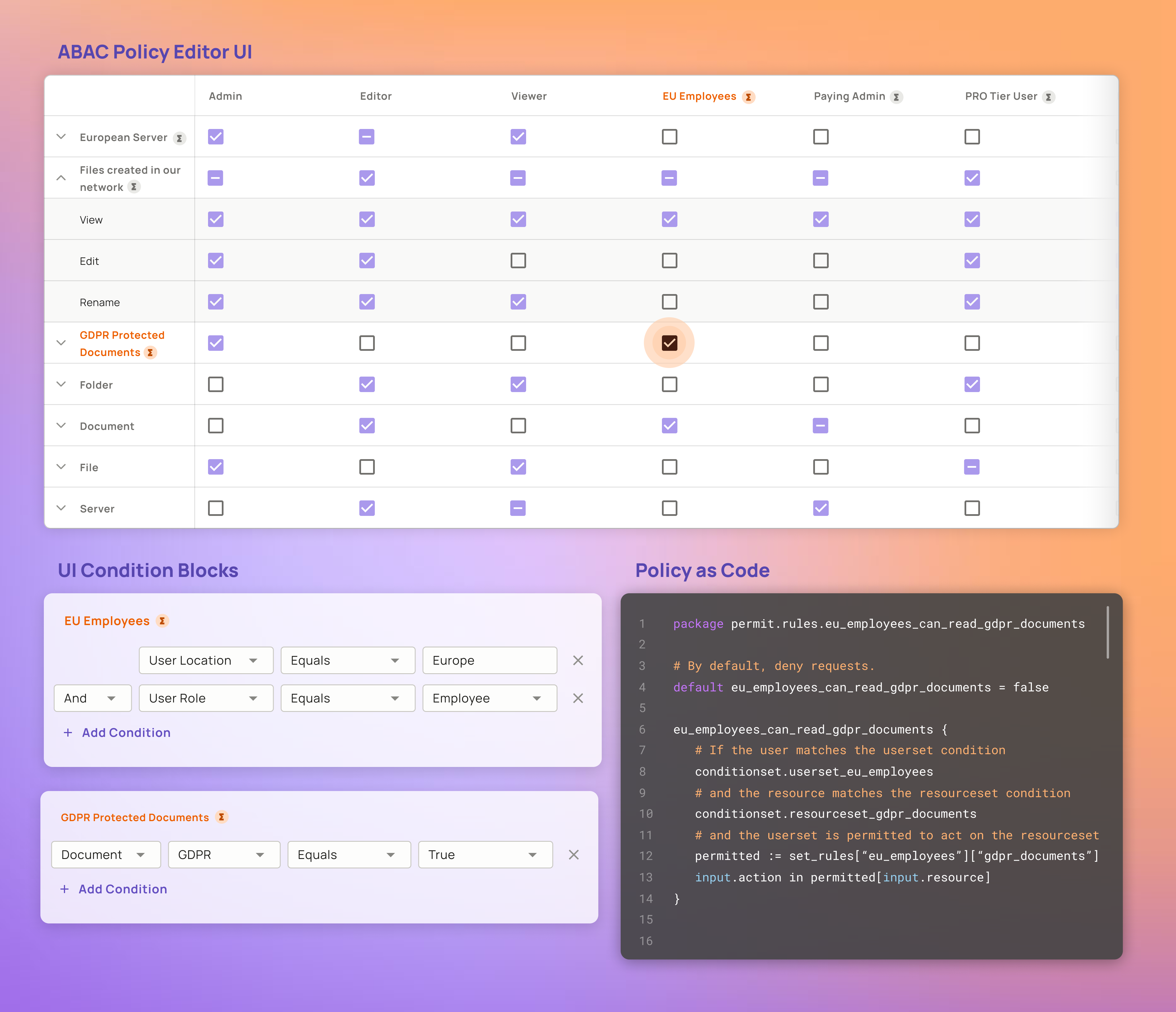

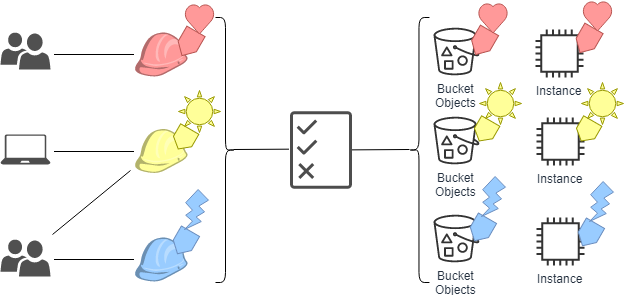
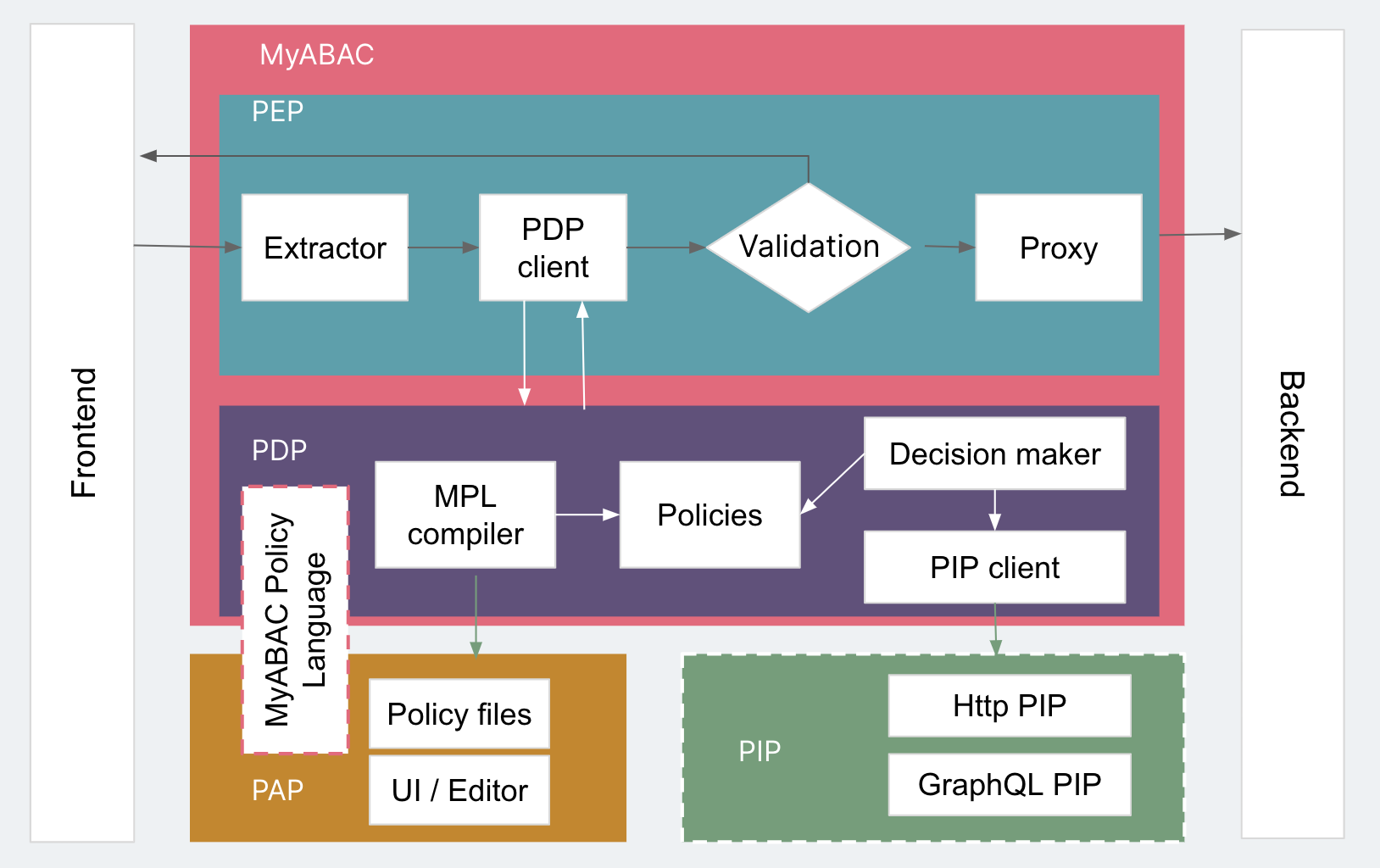
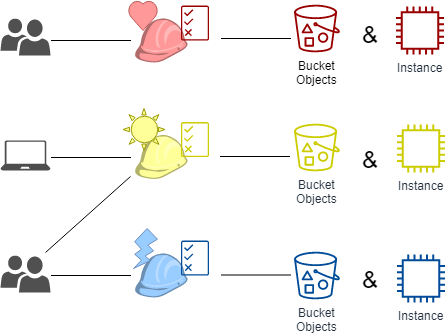
![PDF] Attribute-Based Access Control | Semantic Scholar PDF] Attribute-Based Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f2d698c5a1819b0cff0c8899b8a391c5721aa2b6/2-Figure1-1.png)
